10 Jun 2011 | Index Index, minipost
Former U.S. National Security Agency employee, Thomas Drake, agreed to a plea bargain that will reduce his charges from a felony under the Espionage Act to a misdemeanor for misusing the agency’s computer system. In this new scheme, prosecutors promised not to seek jail time. Drake originally faced a 35-year prison sentence for providing official documents to a reporter for The Baltimore Sun.
10 Jun 2011 | Uncategorized
A Tunisian policeman who blew the whistle on a still-active core of officers from the country’s pre-revolution days — some of them alleged torturers, others linked to Tunisia’s long notorious internet surveillance squads — has been hauled in front of a military court for speaking out. (more…)
10 Jun 2011 | Uncategorized
 Who needs privacy? It’s a human right that isn’t just a concern for the rich and powerful wishing to shield their private lives from the media. Today, it’s an urgent issue for anyone who communicates online. In Privacy is dead! Long live privacy, Index on Censorship assesses the threats to our data, considers the impact of tabloid exposés on press standards, explores the world of internet trolls and talks to the UK’s leading privacy judge about striking the balance.
Who needs privacy? It’s a human right that isn’t just a concern for the rich and powerful wishing to shield their private lives from the media. Today, it’s an urgent issue for anyone who communicates online. In Privacy is dead! Long live privacy, Index on Censorship assesses the threats to our data, considers the impact of tabloid exposés on press standards, explores the world of internet trolls and talks to the UK’s leading privacy judge about striking the balance.
With:
MR JUSTICE EADY on balancing acts
BIRGITTA JÓNSDÓTTIR’s online wake-up call
BRIAN CATHCART on the privacy invaders
GUS HOSEIN & ERIC KING on the age of insecurity
10 Jun 2011 | Asia and Pacific, China
The theft of hundreds of Gmail account passwords last week by Chinese hackers from Jinan city in Shandong province left many of us feeling vulnerable. But there are ways in which to avoid becoming the next victim of a phishing scam.
The official Google blog illustrates how phishing scams work. One post warns against clicking on suspicious links in e-mails:
Always be cautious when clicking on links appearing in instant messages and emails, or when asked to share personal information like passwords online.
If you should accidentally click on such a link, you may be redirected to a log-in page. The security blog, Contagio provides an example of the kind of login page that appears as part of the phishing scam.
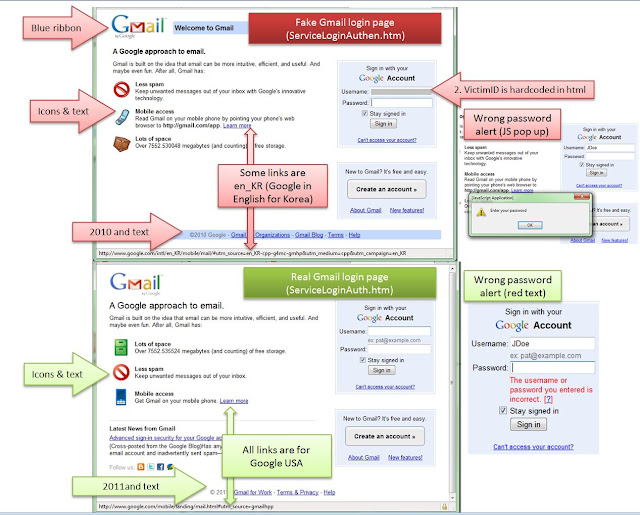
The distinction between “real” and “fake” log-in pages is actually quite clear. Legitimate sites indicate which country the links belong to and the year in which the text first appeared.
Up until this point, the user is safe. But once the user enters his information in the fake log-in page, it is shared with the hackers who can then set up forwarding accounts in the hacked account to further spread the scam. Further, all mail received by that account is sent to a separate inbox set up by the hackers.
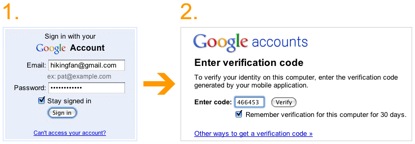
The official Google blog recommends obtaining a verification code set up via your mobile phone, so that you know when you are entering the “real” Google login page.
Also, Google encourages users to check under the “Forwarding and POP/IMAP” option in their e-mail accounts. If an unknown email address is spotted, then the account has been hacked.